Managing Segregation of Duties (SoD) risks is a critical component of enterprise governance and compliance. While applying mitigation controls is a significant first step, the real challenge lies in how organizations monitor and manage these risks post-mitigation to ensure ongoing security and compliance.
Introduction
To explore on this topic more detailed, we conducted a LinkedIn poll:
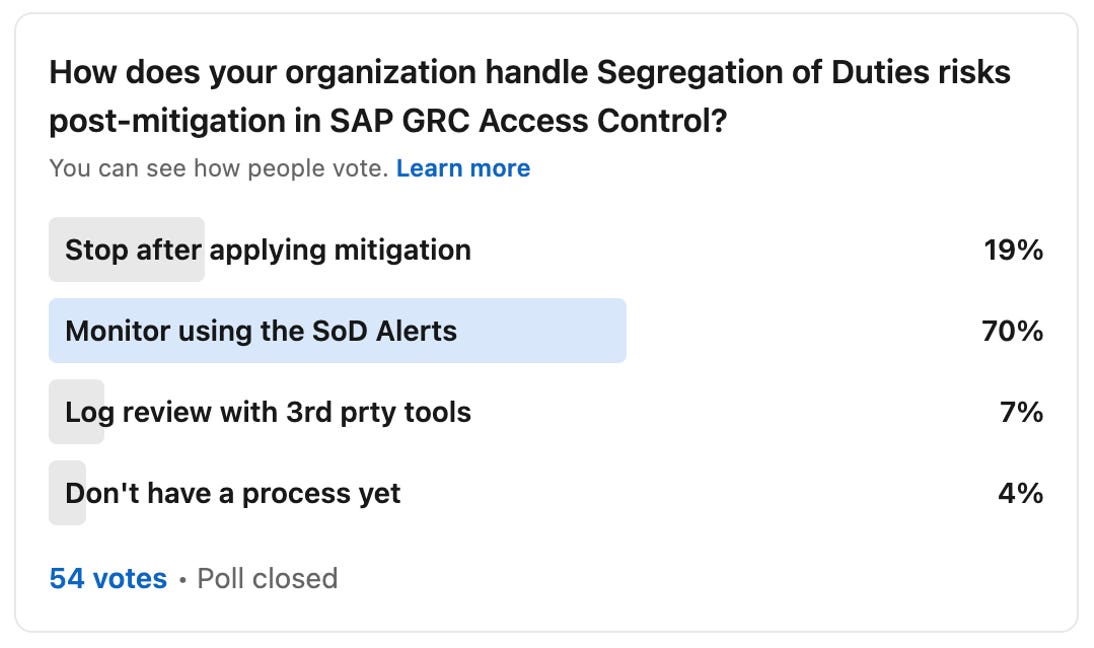
Question: How does your organization handle Segregation of Duties risks post-mitigation in SAP GRC Access Control?
The poll received 54 responses (fortunately, no robot responses), providing first level insights into the current practices and trends in the industry. The results were eye-opening:
70% of respondents rely on the SoD Alerts feature in SAP GRC Access Control to monitor and manage these risks proactively.
The remaining responses were split between other approaches, such as stopping after applying mitigation, using third-party tools for log reviews, or not having a defined process yet.
Have a look at the response split:
The SoD Alerts feature in SAP Access Control is a powerful tool designed to notify stakeholders when conflicting or critical transaction codes are executed. These alerts empower organizations to:
Quickly respond to potential risks.
Maintain compliance with regulatory standards.
Safeguard critical systems from security breaches.
However,
How diligently do Mitigation Monitors or Owners review the alerts?
Are sufficient evidences collected and analyzed when alerts are triggered, or do they simply fulfil a procedural checkbox?
How are the evidences documented for future reference and audits?
Does the controller reach out to the business user to gather additional evidence when needed? Has this occurred in your enterprise?
What actions or decisions typically follow when a conflicting alert is identified?
To better understand, let’s consider an example:
User A has been assigned with two conflicting transaction codes - Transaction Code - F-43 (Enter Vendor Invoice) and F-53 (Post Outgoing Payments)
The conflict arises because F-43 allows users to enter vendor invoices, while F-53 allows users to make payments to those vendors. If a user has access to both, they could potentially create a fraudulent invoice (via F-43) and then process a payment (via F-53) to themselves or an unauthorized party. This creates a significant risk of financial fraud or errors.
Now when user executes these conflicting transaction codes, an alert is triggered to the controller for further review. These alerts can be accessed from GRC NWBC Access Management Access Alerts Conflicting and Critical Access Alerts or Access Management Access Alerts Mitigating Controls.
Note: This blog does not cover the steps for setting up alerts, as it goes beyond the scope of the topic. It is assumed that readers are already familiar with the process of mitigation and alert configuration. If not, refer to the references provided at the end of this article.
Here’s the real question: What’s next?
Remember, applying a mitigating control and receiving an alert is just the beginning of the journey. The true steps lies in ensuring that the mitigation remains effective, sustainable, and integrated to the broader risk management framework.
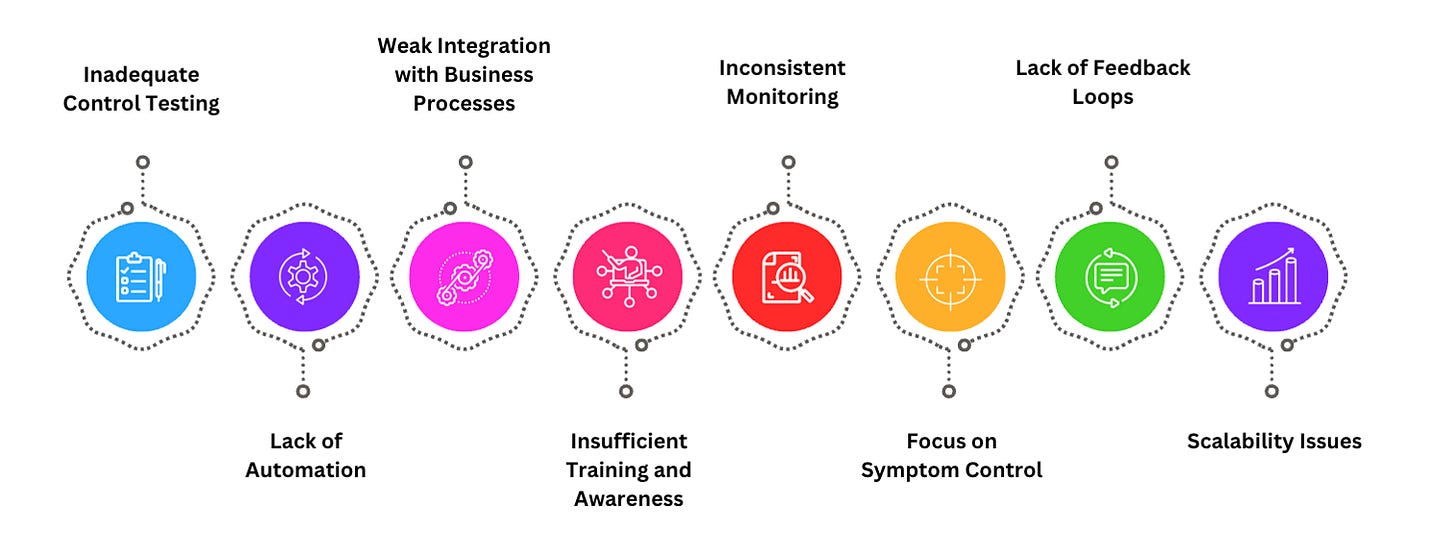
What is Missing?
While enterprises often follow a structured approach to mitigate risks, there are several gaps that can undermine the effectiveness of the post-mitigation process. Addressing these gaps is crucial for ensuring that risk mitigation is both robust and sustainable.
The fact is that 9 out of 10 organizations fall into at least 4 challenges from the above list.
How Can Enterprises Ensure Effective Mitigation?
When it comes to effective mitigation, it's crucial to break the process into two core areas:
Enhancing Access Control Capabilities
Improving the Overall Process
Let's explore each area in detail:
Enhancing Access Control Capabilities
Effective mitigation starts with robust access control systems. Enterprises should:
Regularly update role definitions and permissions to align with evolving business needs.
Setup alerts to High and Critical risks
Generate periodic mitigation and usage reports
Send notifications to the controls that are set to expire soon
Regularly update role definitions and permissions to align with evolving business needs.
Regularly updating role definitions and permissions is crucial to ensure that access controls in an organization remain relevant and secure. As business evolve, the roles and permissions assigned to users must also be changed. This ensures that employees have the necessary access to perform their job duties, while also maintaining the principle of least privilege.
By reviewing and adjusting roles periodically, businesses can prevent unauthorized access, reduce security risks, and ensure compliance with internal policies and external regulations. Staying proactive in this area helps the organization respond to changing business requirements and emerging threats.
Setup alerts to High and Critical risks
Many enterprises doesn’t even think of utilizing this feature. It is recommended setting up alerts for High and Critical risks as proactive monitoring of potential threats in your SAP environment is important. These alerts notify administrators of unauthorized activities, Segregation of Duties (SoD) conflicts, or critical access violations, enabling timely action to monitor risks. By configuring thresholds and notifications, organizations can enhance compliance, reduce security vulnerabilities, and maintain a robust control framework. This feature is pivotal for safeguarding sensitive business data and meeting regulatory requirements. Regular reviews and fine-tuning of alerts ensure they remain effective and aligned with evolving business needs.
Generate periodic mitigation and usage reports
Generating periodic mitigation and usage reports in SAP Access Control provides critical insights into how risks are managed and controlled over time. Mitigation reports highlight the effectiveness of applied risk mitigation controls, while usage reports track how critical access is being utilized.
These reports help organizations ensure compliance with regulatory requirements, identify potential misuse or gaps in controls, and maintain accountability. Automating these reports streamlines the review process, enabling stakeholders to take timely, data-driven actions to strengthen security and governance.
SAP GRC offers few reports to identify the invalid mitigation controls. However, further customizations can be made for a better reporting.
NOTE: ToggleNow GAMS360 (GRC Audit Management Systems 360) offers various reports for better management of mitigating controls and risks.
Send notifications to the controls that are set to expire soon
How are you handling the mitigations that are near to expiry? Is it manually handled today? If yes, you may use the report – GRAC_EXPIRE_MITIGATION_CONTROL (refer to SAP Note 3447279) – From SP24, which will send notification for those controls that are set to expire soon. The earliest email can be sent within the first 15 days.
NOTE: ToggleNow customized these reports to fit in the business requirements. For example, after the initial notification, a follow-up will be sent to the respective stakeholders too.
Improving the Overall Process
While technology plays a critical role, the effectiveness of mitigation heavily depends on the supporting processes. To ensure a comprehensive approach, enterprises should focus on the following key steps:
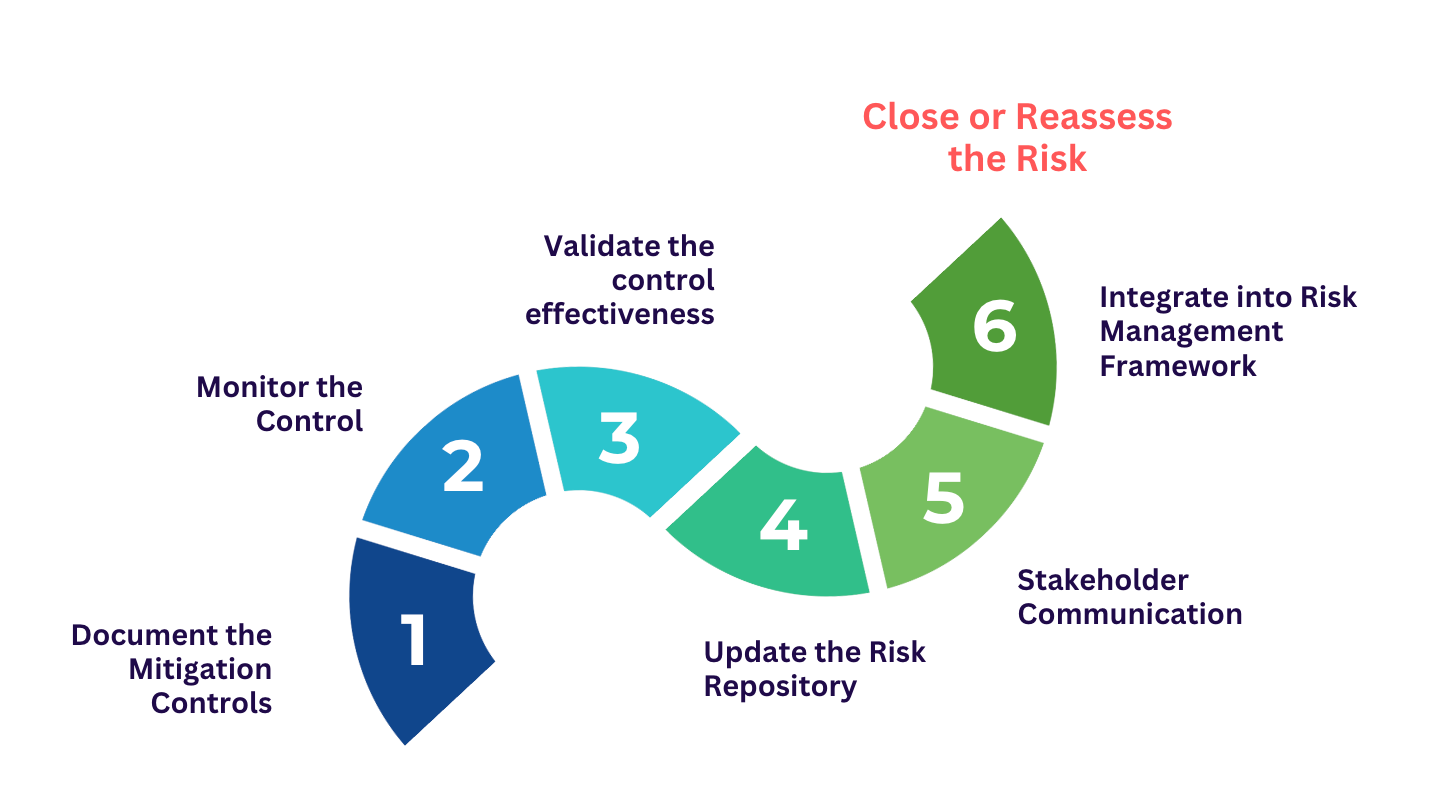
Document the Mitigation Measures
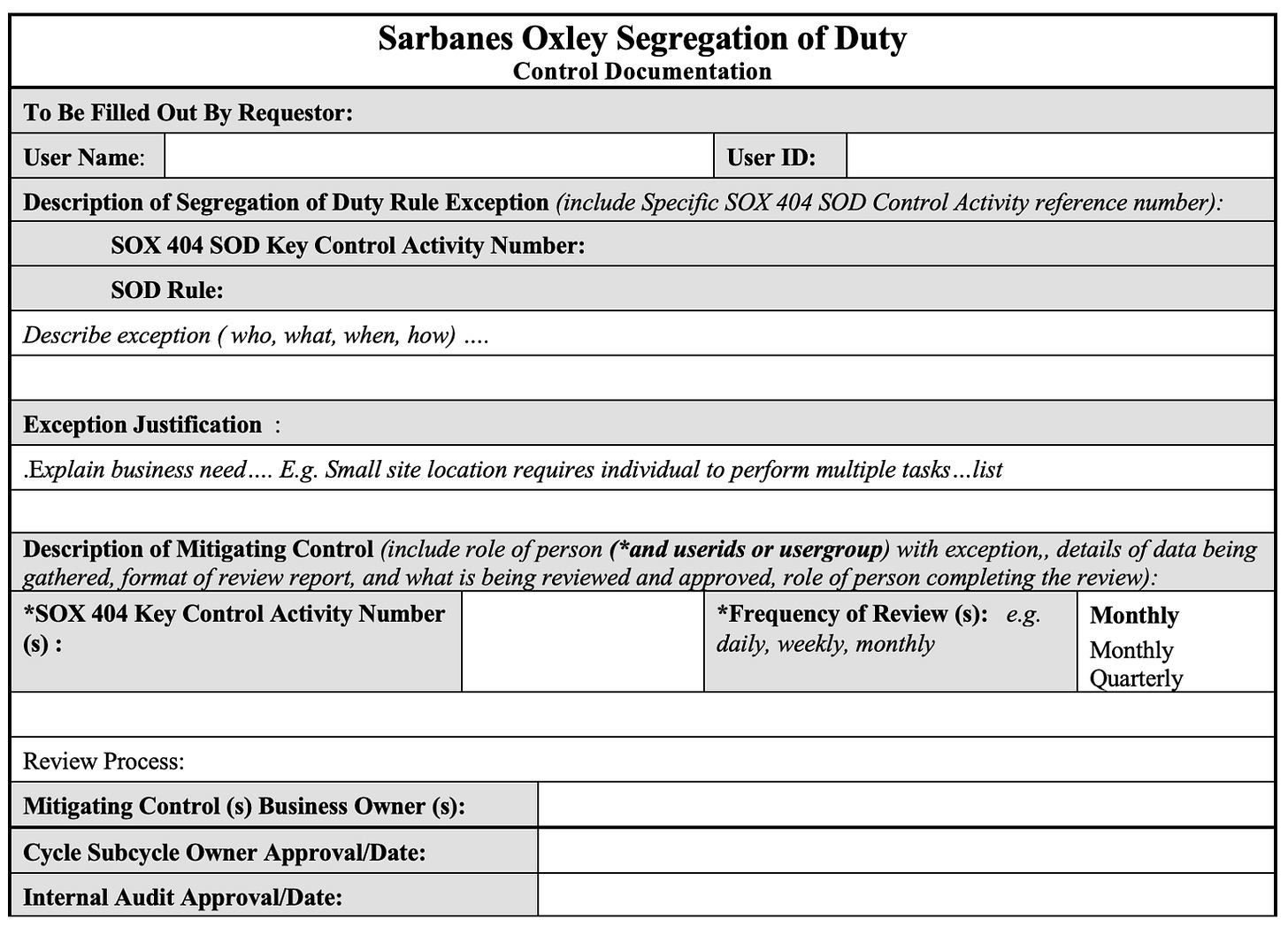
The first step after applying a mitigation is to document the control thoroughly. This documentation should detail:
The nature of the control (What is the risk, why it can’t be remediated? Why an exception etc.,)
The roles and responsibilities of individuals involved (such as Reviewer, Primary Owner, Sub-cycle owner, Internal Audit team etc.,)
The process (Review process, frequency of the review, documentation requirements etc.,)
Clear documentation is not only critical for audit purposes but also helps maintain a historical record for future reference. It ensures that mitigation actions are traceable, auditable, and aligned with the organization’s compliance requirements. This documentation will also serve as a reference point for future risk assessments or when the control needs to be reviewed or updated. Here is an example:
Monitor the Control
As mentioned earlier, mitigation and documentation is the first step. Once a control is established, it requires monitoring as per the agreed frequency to ensure its effectiveness. This is where the organization must remain vigilant. For example, if the mitigation involves periodic reviews of user access, it’s important to ensure that these reviews occur consistently and within the defined timeframes. Monitoring can also include examining key performance indicators (KPIs) or alerts triggered by the system when specific thresholds are met.
Validate the Effectiveness
The effectiveness of the control must be validated. This can be done through periodic control testing or validation processes. For instance, reviewing audit logs, conducting user activity tests, or verifying the functionality of the mitigating control are common approaches. Validation checks ensure that the mitigation is not only in place but also operating as intended. If flaws are identified in the system, corrective actions can be taken promptly to prevent further risk exposure.
Update the Risk Repository
The risk repository is the centralized record of all identified risks and mitigation efforts within the organization. Once a mitigation is applied, it should be reflected in this repository to maintain an up-to-date view of the risk landscape. This update includes:
The status of the risk (mitigated, open, etc.).
Details of the mitigation measures applied.
The effectiveness of the mitigation, based on ongoing monitoring and validation.
An updated risk repository ensures that all stakeholders have access to the latest information and helps in decision-making for future risk management activities.
Communicate with Stakeholders
One of the key steps after mitigation is informing relevant stakeholders about the risk mitigation measures and their effectiveness. This includes communicating with:
Auditors: To ensure that the mitigation is aligned with compliance requirements.
Risk Owners: To update them on the status of the risk and provide evidence of effective mitigation.
Internal Teams: To ensure all relevant parties are aware of the changes and their roles in maintaining the mitigation.
Effective communication fosters transparency and encourages collaboration across departments. It also helps in building a culture of accountability in risk management.
Integrate into Risk Management Framework
Align the mitigation measures with the organization's broader risk management framework to ensure consistency and strategic alignment.
Close or Reassess the Risk
After implementing and validating controls, either close the risk if mitigated or reassess it to determine if further action is required.
By focusing on these two areas, enterprises can strengthen their mitigation strategies, ensuring not only compliance but also a secure and resilient operational environment.
Conclusion
Mitigating Segregation of Duties risks in SAP GRC is only the first step in a much larger process. The post-mitigation actions—ranging from documentation and monitoring to integration with broader risk management frameworks—are critical to ensuring that the mitigation remains effective and sustainable. By addressing common gaps such as inadequate testing, lack of automation, and insufficient integration with business processes, organizations can enhance their risk mitigation strategies and build a more robust, scalable, and dynamic risk management framework.
Additional References
SAP Note 2389871 - Customizing Alert Notification e-mails for SOD and Mitigation Control
Rulesets in SAP Access Control - https://blog.sap-press.com/rulesets-in-sap-access-control
SAP Access Control Comprehensive Guide by Raghu Boddu - https://www.sap-press.com/sap-access-control_5636/
SAP Note 2864153 - Explanation of Functionality in Mitigation Control Monitoring and Alerts
User/Role Level Invalid Mitigations – https://help.sap.com/docs/SAP_ACCESS_CONTROL/5cae1bc9a72348389e91183714220e30/486b88264da04f94912b0e2133395017.html




Informative article 👍